
What Is a Man-in-the-Middle (MITM) Attack?
A man-in-the-middle (MITM) attack intercepts communication or data transfer, either by eavesdropping or impersonating a participant, allowing attackers to quietly hijack information without the victim’s knowledge.
In this seemingly harmless setting, hackers can intercept your data as it travels between your device and the internet, potentially accessing your sensitive information like login credentials without your knowledge.
Understanding MITM attacks is crucial for safeguarding yourself online, as it empowers you to recognize and mitigate these threats, ensuring your privacy and security in an increasingly connected world.
- What Is a Man-in-the-Middle (MITM) Attack?
- How Does a MITM Attack Work?
- Real-World Example
- Types of MITM Attacks
- How to Detect a Man-in-the-Middle Attack
- Man-in-the-Middle Attack Prevention
What Is a Man-in-the-Middle (MITM) Attack?
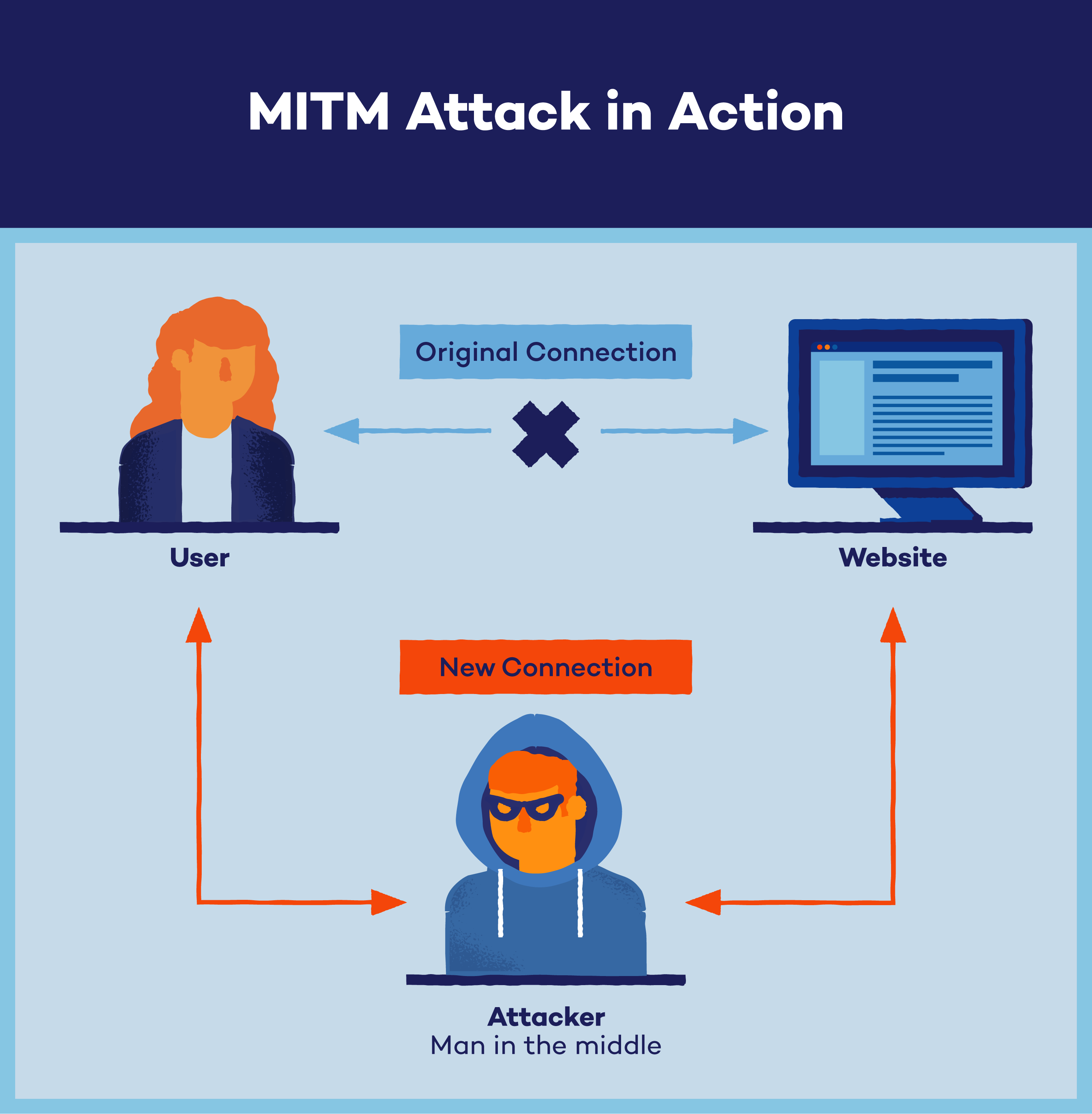
A MITM attack is a type of cyberattack where attackers intercept an existing conversation or data transfer, either by eavesdropping or by pretending to be a legitimate participant. To the victim, it will appear as though a standard exchange of information is underway — but by inserting themselves into the “middle” of the conversation or data transfer, the attacker can quietly hijack information.

The goal of a MITM spoofing attack is to retrieve confidential data such as bank account details, credit card numbers or login credentials, which may be used to carry out further crimes like identity theft or illegal fund transfers. Because MITM attacks are carried out in real time, they often go undetected until it’s too late.
How Does a MITM Attack Work?
Here’s a simplified breakdown of how a MITM attack works in three steps:
- Interception: The attacker sets up a fake Wi-Fi hotspot in a public space, often without requiring a password. When a victim connects to this hotspot, the attacker can intercept any online data exchanges, such as emails and website logins.
- Positioning between victim and destination: The attacker uses techniques like IP spoofing, where they alter IP packets to impersonate the victim’s computer system and redirect the victim to the attacker’s website.
- Decryption: Through techniques like HTTPS spoofing, SSL hijacking and SSL stripping, the hacker decrypts the intercepted data, making the victim’s activity visible to the attacker.
Real-World Example
The Lapsus$ targeting Office 365 incident in 2022 highlights how attackers can combine MITM techniques with social engineering. By spoofing the Office 365 login page, Lapsus$ group stole user credentials and bypassed multi-factor authentication (MFA) to access email accounts.
Types of MITM Attacks
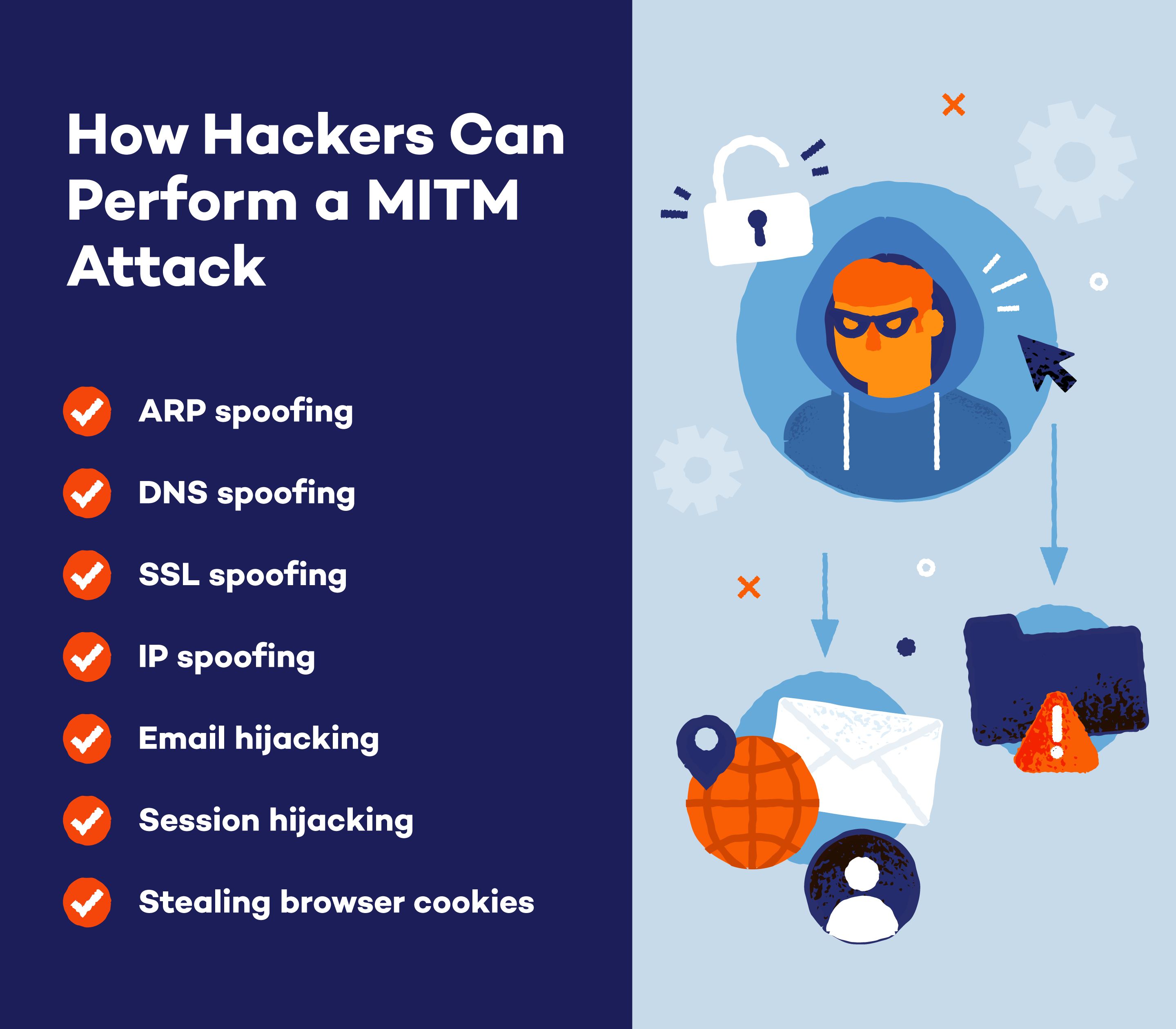
Hackers use various techniques to carry out man-in-the-middle attacks, aiming to intercept and manipulate communication between two parties. Here are some common types of MITM attacks:
ARP Spoofing
ARP spoofing is a technique used by attackers to intercept and manipulate data packets in a network. By sending falsified Address Resolution Protocol (ARP) messages, the attacker links their own MAC address to the IP address of the victim’s device, tricking the network into sending data packets to the attacker instead of the intended recipient. This allows the attacker to eavesdrop on communication, modify data or launch further attacks on the network.
DNS Spoofing
DNS spoofing, or DNS cache poisoning, is a type of man-in-the-middle attack where an attacker alters the information in a Domain Name System (DNS) server to redirect users to malicious websites. By tampering with the DNS records, the attacker can deceive users into visiting fake websites that closely resemble legitimate ones.
SSL Stripping
SSL stripping is a technique attackers use in MITM attacks to downgrade a victim’s secure HTTPS connection to an unsecure HTTP connection.
By intercepting the communication between the victim and the website, the attacker removes the encryption layer (SSL/TLS) from the connection. This makes the victim’s activity visible to the attacker in plain, unencrypted text, allowing them to capture sensitive information such as login credentials, financial details and personal data exchanged between the victim and the website.
IP Spoofing
IP spoofing is a technique in which attackers manipulate IP packets to impersonate the victim’s computer system, redirecting them to malicious websites.
By altering the source IP address in the packets, attackers make it appear as if the data is coming from a trusted source, fooling systems into accepting and processing it. This allows attackers to intercept and manipulate communication between the victim and the intended destination, leading to potential data theft or unauthorized access.
Email Hijacking
Email hijacking occurs when an attacker gains unauthorized access to someone’s email account, often through phishing or malware, and takes control of it without the owner’s knowledge. Once hijacked, the attacker can read, send, and delete emails, as well as access any linked accounts or sensitive information contained within emails. Email hijacking can lead to privacy breaches, financial fraud and even identity theft.
Stealing Browser Cookies
Stealing browser cookies involves attackers intercepting and obtaining the cookies stored on a victim’s web browser without their knowledge.
These cookies contain information such as login credentials, session tokens and browsing history, which the attacker can exploit to gain unauthorized access to the victim’s accounts, track their online activities or impersonate them on websites.
Session Hijacking
Session hijacking is a type of cyberattack where an attacker intercepts and takes over an ongoing session between a user and a website or service.
This typically occurs by stealing the session ID or token used to authenticate the user’s session, allowing the attacker to impersonate the user and gain unauthorized access to their account or data. Once hijacked, the attacker can perform actions on behalf of the user, such as making transactions, sending messages or accessing sensitive information.
How to Detect a MITM Attack: 5 Signs
Detecting a MITM attack can be challenging, but there are several signs to watch for:
- Unexpected HTTPS warnings: If your browser shows warnings about invalid or suspicious HTTPS certificates, it could be a sign that someone is trying to intercept your connection.
- Unusual network activity: An unexpected spike in network activity, slow internet speed or frequent disconnections can indicate a possible MITM attack.
- Strange URLs or website behavior: If you notice odd URLs in the address bar, unusual redirects or websites that look slightly different than usual, it could be a sign that traffic is being manipulated.
- Repeated login prompts: Being repeatedly asked to log in to websites, especially those that normally keep you logged in, can indicate that someone is trying to capture your login credentials.
- Unrecognized devices on your network: Finding unknown devices connected to your network can be a sign that an unauthorized user has accessed your network, potentially facilitating a MITM attack.
If you’re not actively searching for signs that your online communications have been intercepted or compromised, detecting a man-in-the-middle attack can be difficult. While it’s easy for them to go unnoticed, there are certain things you should pay attention to when you’re browsing the web — mainly the URL in your address bar.
Here is how you can check if the website is secure:
- The sign of a secure website is denoted by “HTTPS” in a site’s URL.
- If a URL is missing the “S” and reads as “HTTP,” it’s an immediate red flag that your connection is not secure.
- You should also look for an SSL lock icon to the left of the URL, which denotes a secure website.

Man-in-the-Middle Attack Prevention
While being aware of how to detect a potential MITM attack is important, the best way to protect against them is by preventing them in the first place. Be sure to follow these best practices:
- Avoid Wi-Fi networks that aren’t password-protected, and never use a public Wi-Fi network for sensitive transactions that require your personal information.
- Use a virtual private network (VPN) — especially when connecting to the internet in a public place. VPNs encrypt your online activity and prevent an attacker from being able to read your private data, like passwords or bank account information.
- Log out of sensitive websites (like an online banking website) as soon as you’re finished to avoid session hijacking.
- Maintain proper password habits, such as never reusing passwords for different accounts, and use a password manager to ensure your passwords are as strong as possible.
- Use multi-factor authentication for all of your passwords.
- Use a firewall to ensure safe internet connections.
- Use antivirus software to protect your devices from malware.
As our digitally connected world continues to evolve, so does the complexity of cybercrime and the exploitation of security vulnerabilities. Taking care to educate yourself on cybersecurity best practices is critical to the defense of man-in-the-middle attacks and other types of cybercrime. At the very least, being equipped with a strong antivirus software goes a long way in keeping your data safe and secure.
The post What Is a Man-in-the-Middle (MITM) Attack? Prevention + 7 Types appeared first on Panda Security Mediacenter.